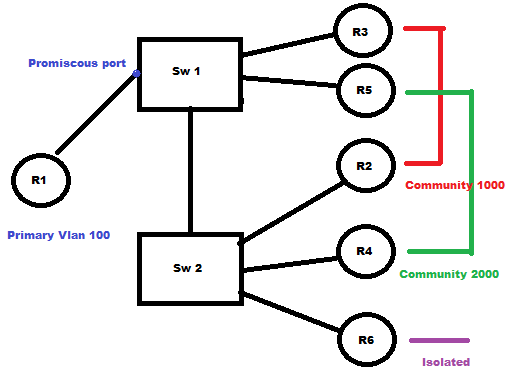
So today i was working on using private vlans and it's such an easy topic but just had many tricks when it comes to configuring it , in the above task we want R1 to be able to ping all routers since its in the primary vlan and its port is promiscous port.
Think of private Vlan as subdividing your vlan into several small vlans in the design above we have sub vlans 1000 and 2000 and isolated vlan 3000
Note that trunking is allowed of course between SW1 and SW2 but let's get down to the configuration because this is the most confusing part. Let's divide the configuration process to 3 parts.
Part 1
Defining VLANS
Think of private Vlan as subdividing your vlan into several small vlans in the design above we have sub vlans 1000 and 2000 and isolated vlan 3000
Note that trunking is allowed of course between SW1 and SW2 but let's get down to the configuration because this is the most confusing part. Let's divide the configuration process to 3 parts.
Part 1
Defining VLANS
This should be applied on switch 1 and switch 2
vlan 100
private-vlan primary
!
vlan 1000
private-vlan community
!
vlan 2000
private-vlan community
!
vlan 3000
private-vlan isolated
!
Vlan 100
private-vlan association 1000,2000,3000 <<<<< Take care we must define VLAN association for the primary vlan and also command won't be accepted before you create vlan 1000 and 2000
Part 2
Applying configuration to community and isolated devices.
Applying configuration to community and isolated devices.
On switch 2
interface FastEthernet0/2 <<< R2
switchport private-vlan host-association 100 1000 <<<<<< Associate primary vlan to community vlan think of it as a device
switchport mode private-vlan host that has access to 2 vlans :)
!
!
interface FastEthernet0/4 <<< R4
switchport private-vlan host-association 100 2000
switchport mode private-vlan host
!
interface FastEthernet0/6 <<< R6
switchport private-vlan host-association 100 3000
switchport mode private-vlan host <<<<<<< Note isolated vlan don't have special config other than the isolated command in vlan definition
On switch 1
interface FastEthernet0/3
switchport private-vlan host-association 100 1000
switchport mode private-vlan host
!
interface FastEthernet0/5
switchport private-vlan host-association 100 2000
switchport mode private-vlan host
Part 3
Applying configuration to promiscous port
Applying configuration to promiscous port
On switch 1
interface FastEthernet0/1
switchport private-vlan mapping 100 1000,2000,3000 <<<<< mapping (primary vlan) add (vlan list)
switchport mode private-vlan promiscuous
Verification
Using only R2 for verification but to verify you should ping R1 to all devices and each community seperatly
R2#ping 100.0.0.4 <<<< R4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.0.0.4, timeout is 2 seconds:
...
Success rate is 0 percent (0/3)
R2#ping 100.0.0.3 <<<<<<< R3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.0.0.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/4 ms
R2#ping 100.0.0.1 <<<<<< R1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.0.0.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms


 RSS Feed
RSS Feed